PalmSecure BioLock PER SAP
- 26 Nov 2016
- PalmSecure BioLock PER SAP
- Fujitsu
PalmSecure BioLock PER SAP
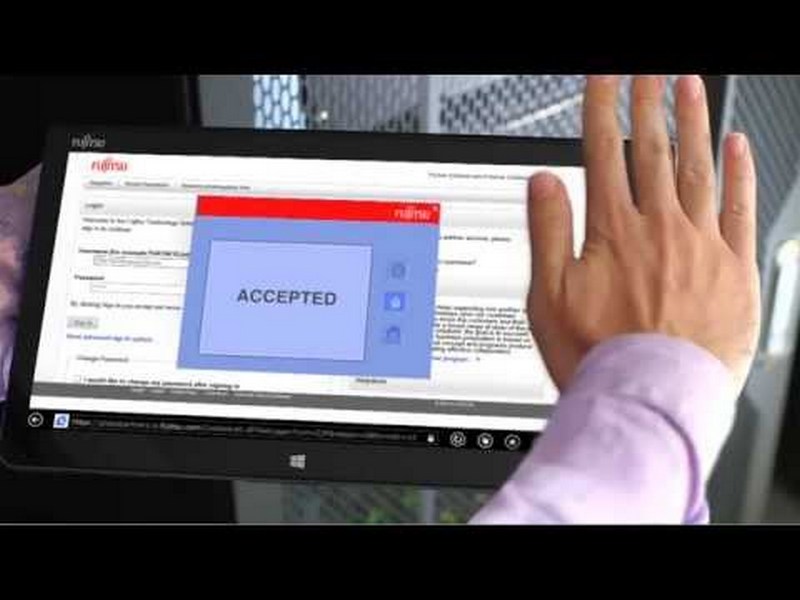
(l’autenticazione biometrica per sistemi SAP ERP e SAP HANA. Fujitsu è ora l’unico SAP Global Partner in grado di offrire questa tecnologia di sicurezza biometrica avanzata sotto forma di soluzione certificata SAP e incorporata nativamente). I clienti SAP di tutto il mondo possono aggiungere un ulteriore livello di sicurezza biometrica ai propri ambienti SAP e proteggere così i propri dati sensibili da furti, perdite e frodi, grazie a una gestione delle identità e degli accessi sicura. Fujitsu PalmSecure bioLock, che è integrato con i classici sistemi di sicurezza SAP come Single Sign-On e SAP Governance, Risk and Compliance (GRC), identifica gli utenti attraverso lo specifico pattern venoso del palmo della mano per controllare il login ai sistemi SAP più critici, che includono risorse umane, CRM, SCM, software finanziari, POS per il retail, nonché la piattaforma SAP HANA. L’autenticazione biometrica permette anche l’accesso sicuro ai sistemi SAP da dispositivi condivisi. Le attività più critiche possono essere ulteriormente protette attraverso checkpoint aggiuntivi di ri-autenticazione biometrica, in modo da garantire che solo il personale autorizzato possa eseguire transazioni critiche. Le caratteristiche nuove e potenziate includono l’autenticazione biometrica per il controllo dell’accesso fisico alle aree riservate delle sedi aziendali, e l’integrazione completa con il modulo SAP Time and Attendance.
SCARICA PDF presentazione :
Version inglese :
palmsecure-biolock PalmSecure bioLock inglese PDF
Versione italiana tradotta automaticamente :
PalmSecure bioLock Italiano PDF
PalmSecure bioLock
Benefits of PalmSecure bioLock
- Protecting and controlling of sensitive data and transactions
- Secured and audit proofed evidence of transactions
- Easy and practicable for users, hygienic, high user acceptance
- Easy integration into existing infrastructure
Pain Points ■ Unresolved Fraud Incidents ■ Violations of segregation of duties despite use of single sign-on (SSO), and governance, risk & compliance (GRC) ■ High cost of IT support, password re-sets Requirements ■ Attain true identity management ■ Eliminate non-authorized users, former employees or other “ghost workers” ■ Provide robust audit trail of all accesses to SAP ■ Achieve 100% SAP perimeter access control Recommendations ■ Enroll all authorized users with biometric profiles. ■ Add a 2nd factor of security for every user at every log-on. ■ Analyze log of SAP accesses to detect fraud attempts. Business Use Case bioLock™ Background This business use case outlines the primary focus of a security program, which is to establish a perimeter excluding anyone who is not authorized. This may mean only your active employees, or may be extended to include specific customers, certain vendors or also contract workers. In SAP, some “users” are actually generic accounts such as SAP* and DDIC, which are not actually individual users. Using such a generic account in combination with powerful profiles such as SAP_ALL can result in a “Backdoor” which can penetrate your perimeter. These generic accounts cannot be easily tied back to a physical employee that can be held accountable. Typically, IDs are created more often than they are deleted. No administrator wants to accidentally delete an ID without being 100% sure the ID is no longer active – and how can you be 100% sure? Symptoms of perimeter weakness – ask yourself: ■ Can we identify if somebody created user IDs that do not correspond to legitimate employees, customers or vendors? ■ If such user IDs were created, do we have an audit trail of who was responsible? ■ If the creators of such IDs have become “ghost workers” not affiliated with the organization, can you prevent them from still logging in? ■ Is there a log of activities done with those IDs? ■ Are there pre-defined expiration dates of those IDs? ■ If “ghost workers” are able to access your SAP data, would you know if they copied any data? ■ If “ghost workers” were able to execute financial operations or other fraud, would you know who did it? ■ Can you restrict the physical locations from which an employee may log in? If you answered NO to any questions, you may have serious gaps in your perimeter security. B
The bioLock™ software from realtime AG introduces true identity management in SAP. As 2nd factor of security bioLock offers a proven Biometric Identity Management that gives you complete control of your SAP perimeter. Existing SAP security, roles and authorizations are unchanged – bioLock software complements, reinforces and resides on top of existing SAP security and GRC. Thus, SAP users can easily attain true system perimeter control by implementing biometric identity management. The bioLock software is the only biometric security program available featuring seamless integration and certification for SAP since 2002.
